authentik version 2025.10 is here!
authentik is an open source Identity Provider that unifies your identity needs into a single platform, replacing Okta, Keycloak, and Ping. Authentik Security is a public benefit company building on top of the open source authentik project.
The 2025.8 release blog post was never posted. Curious about what you missed? Check the 2025.8 release notes.
This release of authentik brings some big features that you don't want to miss, including the addition of our most requested source provider.
Let’s take a closer look at what’s in the 2025.10 release of authentik, your favorite identity provider.
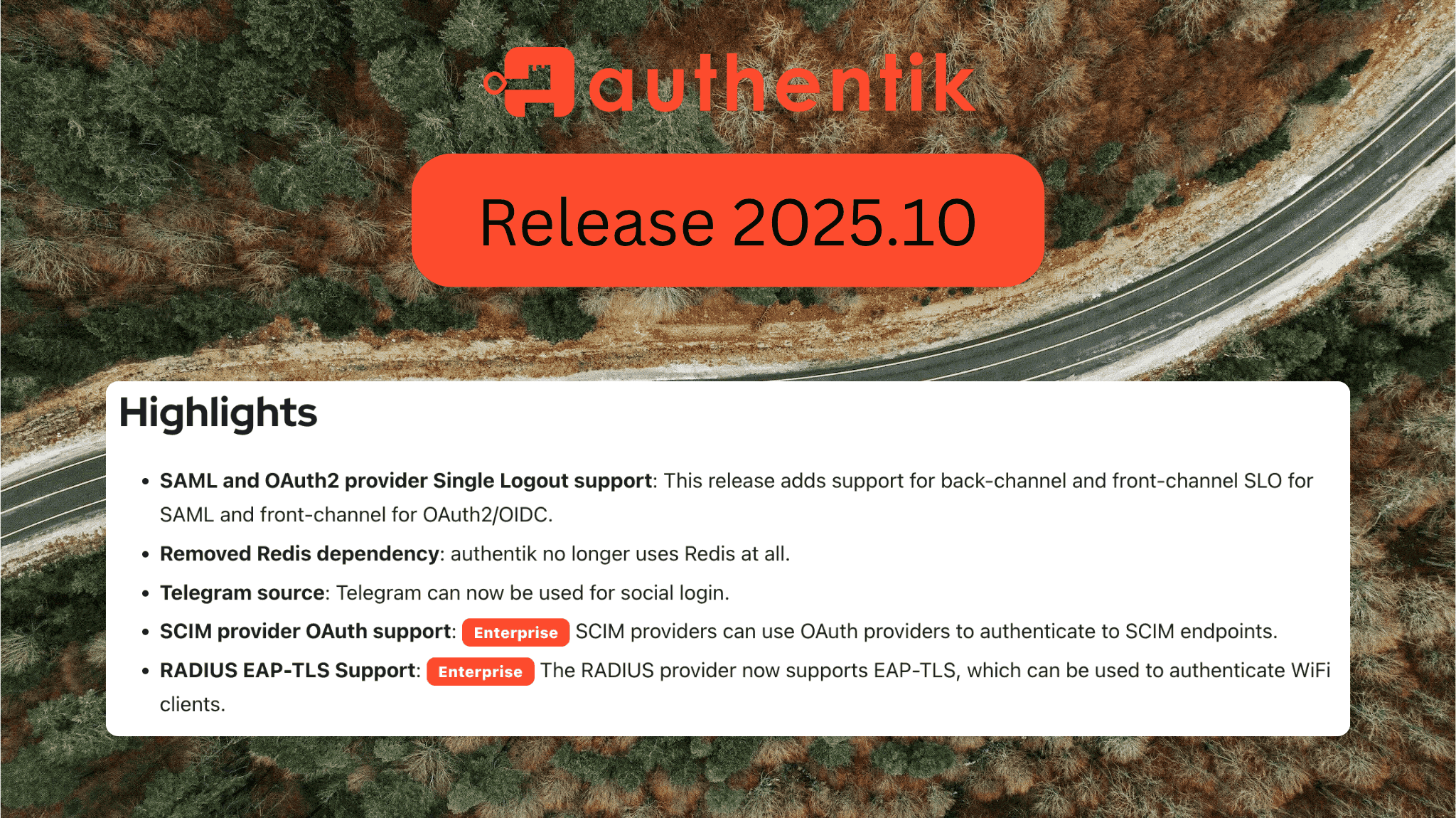
New features
-
SAML and OAuth2 provider Single Logout (SLO) support: This release adds support for Single Logout (SLO), with back-channel and front-channel SLO for SAML and front-channel SLO for OIDC, expanding on our previous addition of OIDC back-channel logout last release. Read our single logout blog post to learn more about this feature.
-
Telegram source: One of our most requested authentication sources, Telegram, has been added with this release. You can now log into authentik using your Telegram account. Thank you atereshkin for adding this!
-
Removed Redis dependency: authentik no longer uses Redis in its tech stack. All features that relied on Redis are now handled by PostgreSQL. To avoid any breaking issues while upgrading, read the section below on Redis removal.
Enhancements
-
SCIM provider now has OAuth token support (Enterprise): SCIM providers can now authenticate using existing OAuth sources instead of static bearer tokens. This enables automatic token rotation and centralized credential management, with authentik handling token lifecycle and refresh automatically.
-
RADIUS EAP-TLS Support (Enterprise): The RADIUS provider now supports EAP-TLS, using the mTLS stage, to authenticate WiFi clients. Learn more in our RADIUS docs.
-
Credential provider: Our desktop integrations are now in alpha releases for testing. Please reach out to hello@goauthentik.io if you are interested in providing early feedback for any of these:
- Windows: a custom credential provider allowing custom authentication flows.
- macOS: a Platform SSO integration allowing seamless authentication.
- Linux: accessing Linux servers via an authentik identity.
-
Send emails using expression policies with
ak_send_email: You can now send emails in expressions by usingak_send_email. Read the expression policies documentation to get started.
Changes to be aware of
We have made a couple breaking changes this version. Be sure to read along and make any updates as needed.
-
Redis removal:
- In previous versions, authentik used Redis for caching, tasks, and WebSocket connections. Since 2025.8, tasks were migrated to use Postgres. With this release we've also migrated caching and WebSocket to Postgres, fully removing the need for Redis.
- If your Postgres instance requires a TLS connection, authentik now requires TLS 1.3 or the Extended Master Secret extension to connect to Postgres.
-
Default OAuth scope mappings:
- In previous releases, in the default scope mappings we set the
email_verifiedclaim totrue. Because we don't have a single source of whether a user's email is verified or not, and claiming that it is verified could lead to security implications, this claim has been corrected tofalse. - Some applications may require this claim to be
trueto successfully authenticate users, in which case you can create a customemailscope mapping that returnsemail_verifiedastrue.
- In previous releases, in the default scope mappings we set the
New integration guides
We have added several important integration guides, with instructions for how to configure authentik SSO for important applications such as Cloudflare, Digital Ocean, Entra ID SCIM, and many others. To all the community members who add these integration guides, thank you for these contributions!
If you have an integration guide you'd like to add, please make a pull request.
Upgrade to version 2025.10
Refer to our Upgrade documentation and the Release Notes for detailed instructions.
Enjoy the new release, and as always, reach out to us with any questions or feedback! Connect with us on GitHub, Discord, or with an email to hello@goauthentik.io.
