Authentik release 2025.4
authentik is an open source Identity Provider that unifies your identity needs into a single platform, replacing Okta, Keycloak, and Ping. Authentik Security is a public benefit company building on top of the open source authentik project.
With every authentik release, we highlight our commitment to delivering new features that focus on providing solutions for all of our users and the identity management challenges that they face.
Our 2025.4 release of authentik contains new features around increased configuration options for authentik Admins, with a new password history policy, the ability to pre-define a bundled set of permissions, setting reputation score limits to further harden access control, and a new "remember me" option.
This release also provides support for PostgreSQL connection pools, the Kubernetes Gateway API, and the ability to do lookups of LDAP group memberships based on user attributes.
Let's take a closer look at a few of these features.
New features
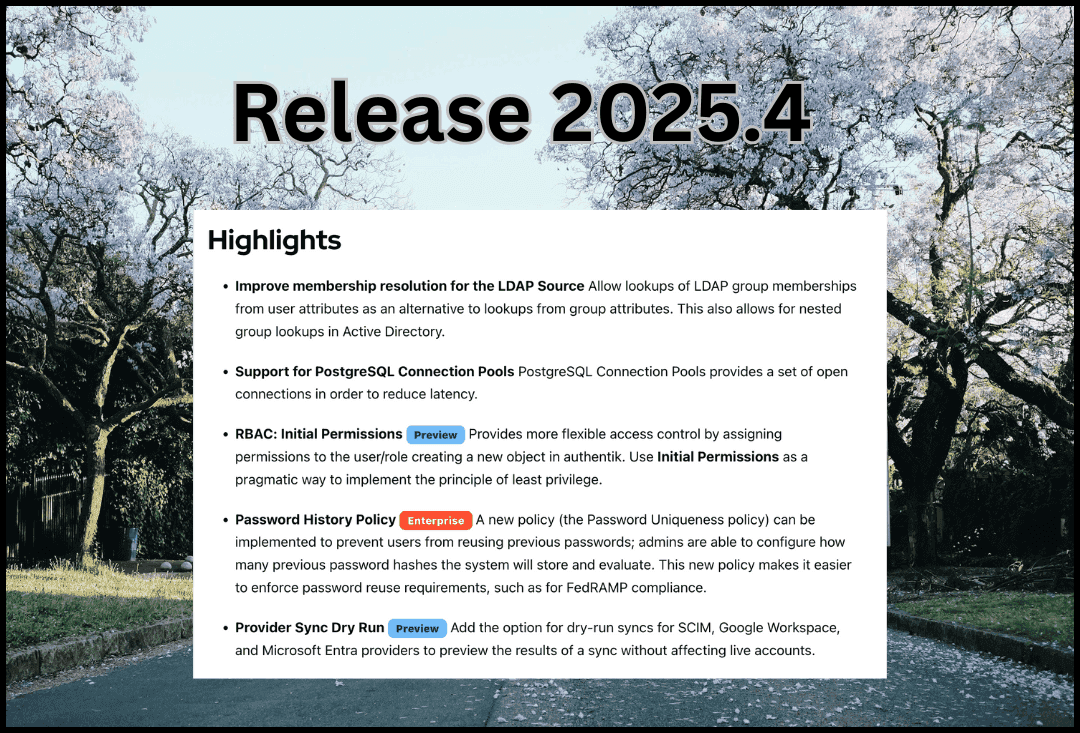
Initial Permissions
This feature allows authentik administrators to proactively define a set of object-level permissions for a user or a role. This prevents a situation where a user (or a group of users with a specific role) might have permission to create an object type, but not to then manage (view/change/delete) that object. Initial Permissions is a mechanism to automatically add pre-selected permissions to any object on creation. For more information, and instructions for implementing Initial Permissions, refer to our documentation.
Reputation score limit
Reputation scores now have a configurable numerical limit in addition to the already existing temporal limit. With the new score limit, an administrator can control the displayed value of the score; for example, no matter what the actual success rate (and thus high score) for a user is, the displayed value can be configured to not be above a specified number. This is a hardening strategy for an instance; you would not display unusually high reputation scores, because that might reveal a potential target.
Password History Policy
An authentik administrator can configure whether a user can re-use a password that they used in the past, or if a password must be new and unique in the history of past passwords. Administrators can define, within the policy settings, how many passwords back in the user's password history to assess. This can help with enforcing compliance requirements, for instance in FedRAMP environments. Refer to our Password Uniqueness Policy documentation for more details.
Improve membership resolution for the LDAP Source
Lookups of LDAP group memberships based on user attributes are now supported, as an alternative to lookups from group attributes. This also allows for nested group lookups in Active Directory.
Remember me option
Users can now choose to skip entering their usernames after their first login on the same device. This feature is optional and administrators can enable it in the Identification stage.
Gateway API support Preview
For Kubernetes users, authentik now supports the Gateway API. The Helm chart supports HTTPRoute. The Kubernetes outpost integrations supports creating HTTPRoute objects for Proxy providers. Refer to our documentation for more details.
Support for PostgreSQL Connection Pools
Using these connection pools provides a set of open connections in order to reduce latency. Refer to our documentation for more information.
Provider Sync Dry Run
This feature provides an option for dry-run syncs for SCIM, Google Workspace, and Microsoft Entra providers to preview the results of a sync without affecting live accounts.
Changes to be aware of
The following points should be considered before updating to version 2025.4 as potentially breaking changes (depending on your current instance's configurations):
-
Be aware that with the new ability to set a lower and upper limit for reputatation scores, there is the potential to break existing custom policies that rely on the reputation scores decreasing or increasing beyond these limits.
-
Helm chart dependencies (PostgreSQL and Redis) will now be updated with each release. Refer to the Release Notes for more details about this change in 2025.4 and in future releases.
-
The
:latesttag is now deprecated and no long supported. We strongly recommended the use of a specific version tag for authentik instances' container images, such as:2025.4. -
Instance sessions are now stored by default in the database, not in cache. Note that on high traffic instances, requests to old instances after the upgrade has started will fail to authenticate.
Upgrade to 2025.4
Refer to our Upgrade documentation and the Release Notes for detailed instructions.
Enjoy the new release, and as always reach out to us with any questions or feedback. Connect with us on GitHub, Discord, or with an email to hello@goauthentik.io.
