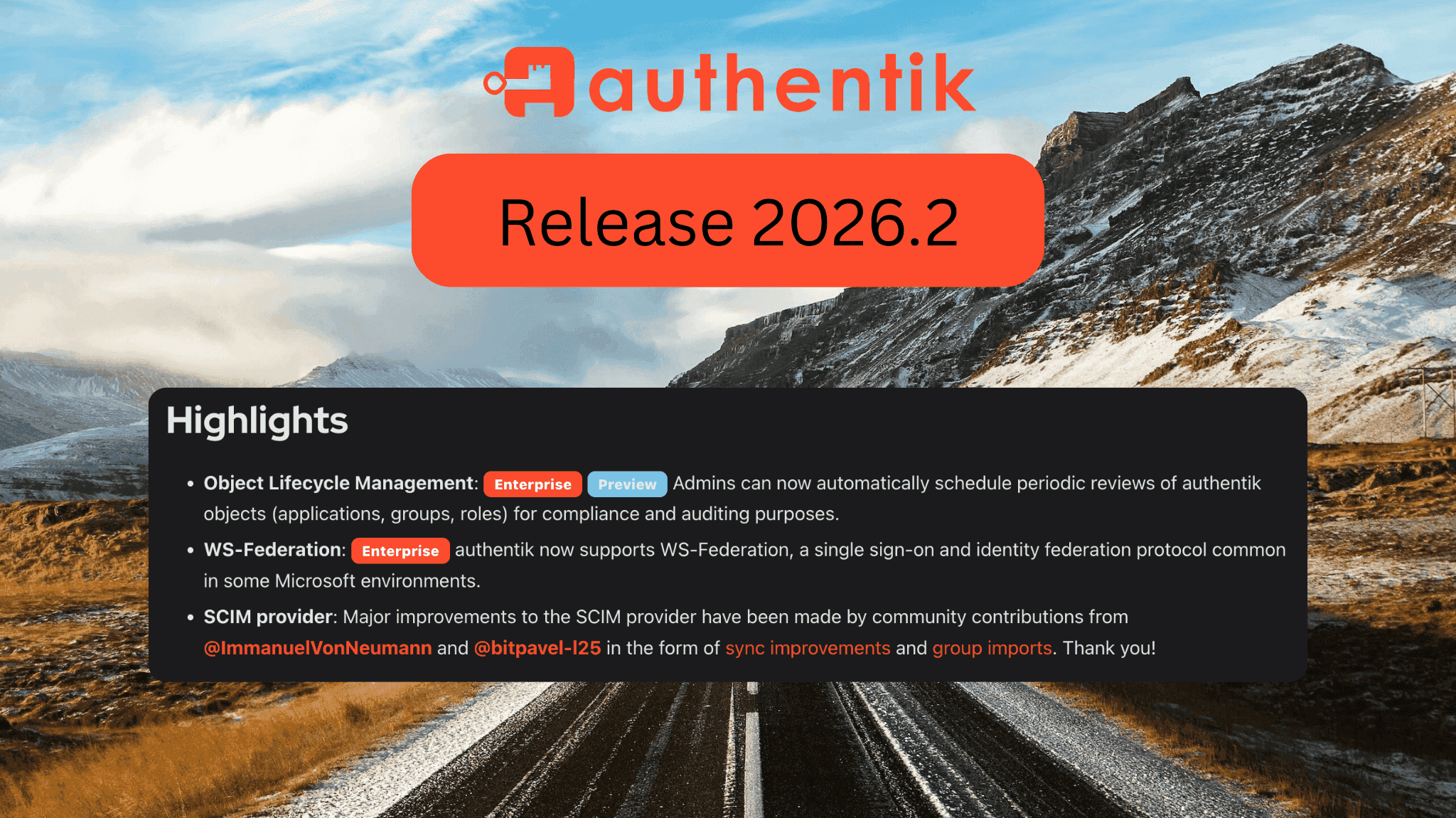
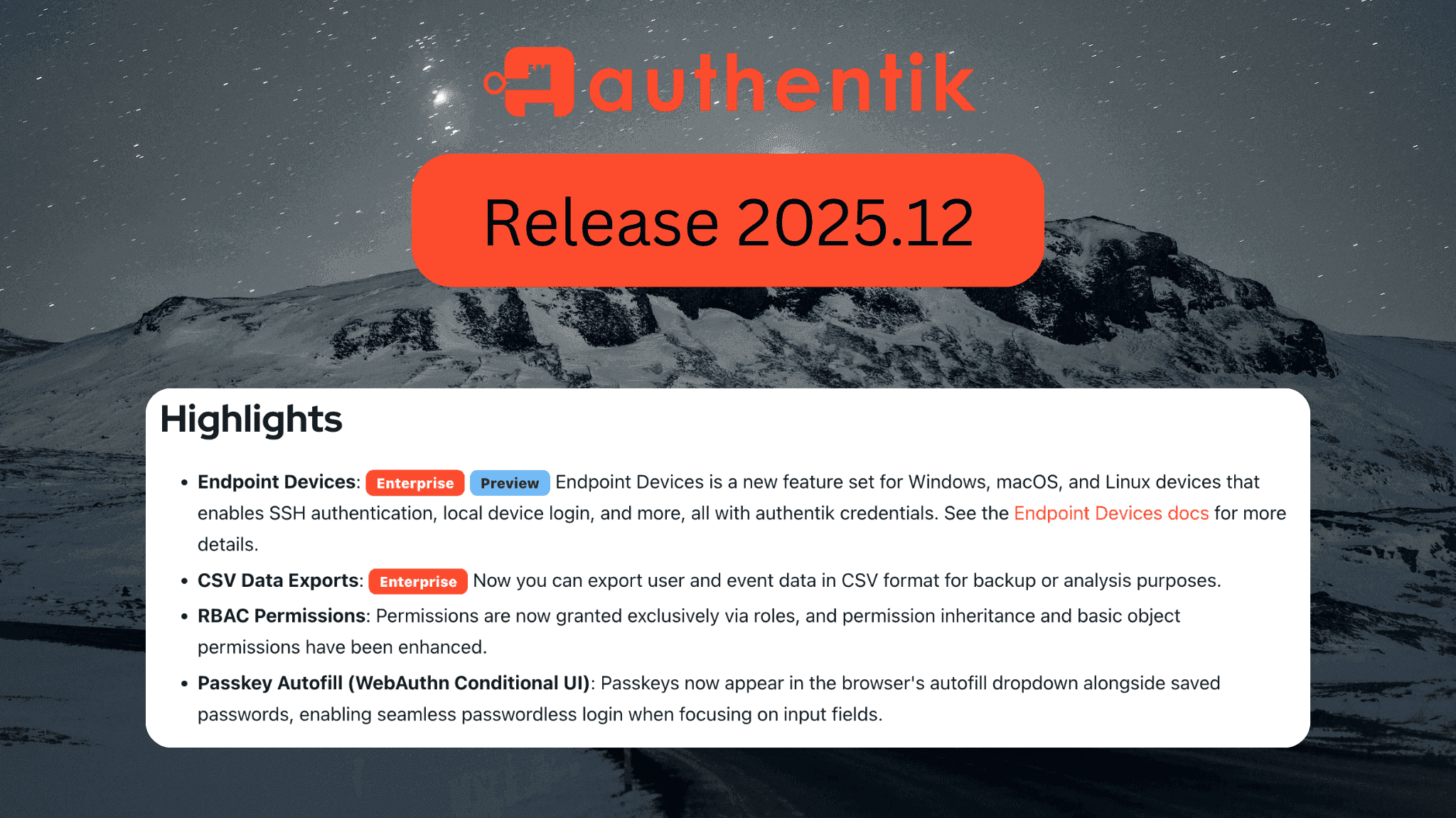
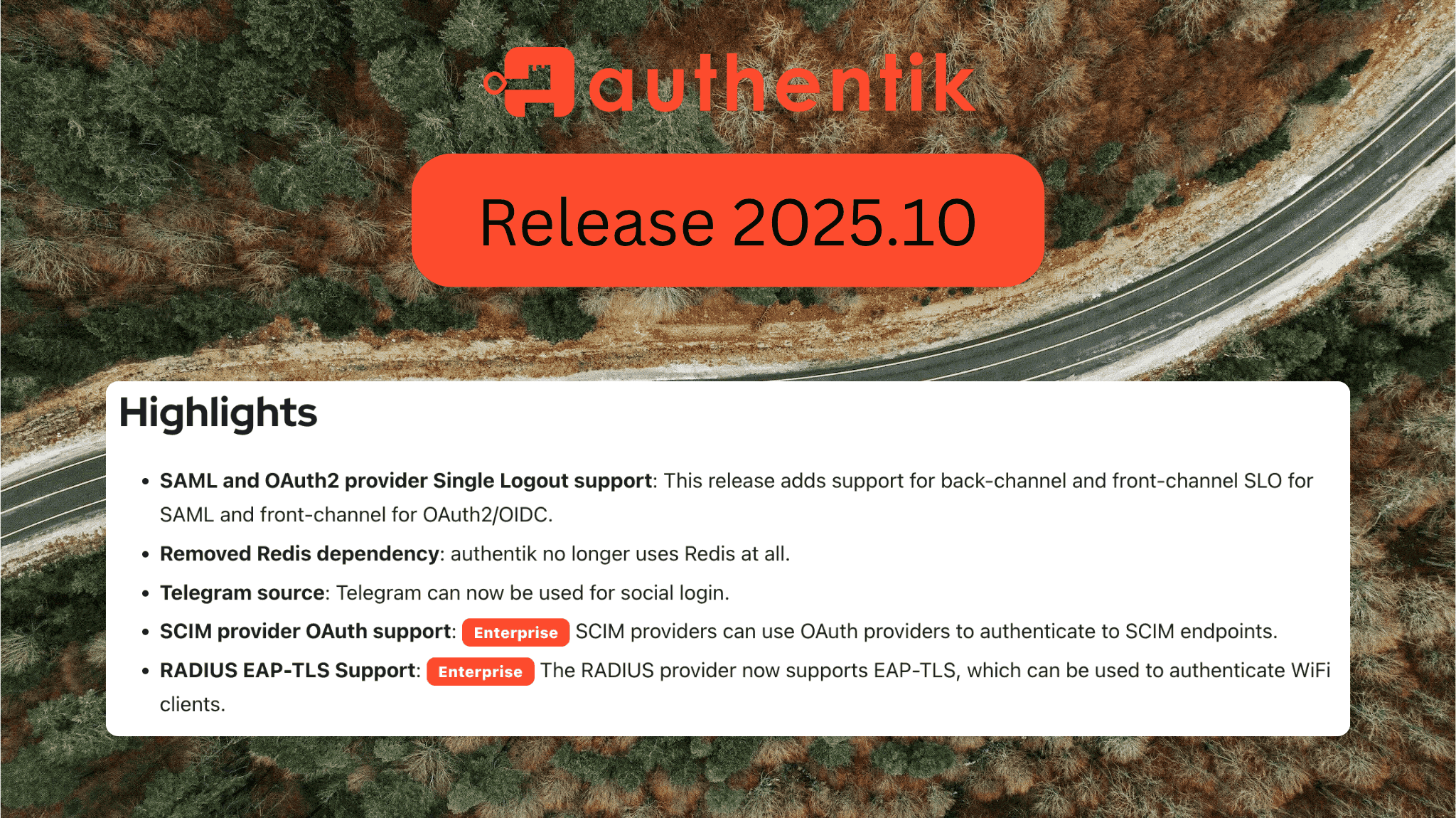
When organizations evaluate Identity and Access Management (IAM) solutions, there are a lot of dimensions to consider: product capabilities, reliability, customer support, operational complexity, compliance, and more.
Practically, one major consideration for any organization considering an enterprise rollout is the total cost of ownership. And unfortunately, the "sticker price" is rarely the full story.
Once you start adding up common real-world requirements for a modern Identity Provider - basics, such as adaptive security, API access, support for workforce versus customer identity management, and the operational costs of integrating the platform, the true total cost can be substantially higher than expected.
At Authentik Security, we have a lot of conversations with customers who initially compare Okta's base "$X/user/month" price to our own Enterprise pricing when considering the cost of a new rollout. We have just as many conversations with long-time Okta users - those looking to migrate away from Okta - who have often found the true cost of ownership to be many multiples of their original quoted starting price.
Any sufficiently large enterprise contract will likely include some custom terms and volume discounting from any vendor, so the following is not meant to be an exact dollar-for-dollar comparison that can apply to any situation. But given the unexpected Okta pricing journey we've heard from many disgruntled customers over time, I felt it was worth attempting a fair comparison of costs in more detail than might be easily gleaned from a pricing page.
Let's break it down by category: